Tuesday, August 17, 2010
Public DNS Service from Google
Google is on its way to establish monopoly on the Internet with the public DNS service.DNS (Domain Name System) in simple word is a set of protocols that translates IP address into names.Every computer on the Internet has an IP address.Thus, the server which is to be accessed by the client, must have have its IP address translated to a name.Like, when we type www.google.com it points to the IP address of the Google server.
Google Public DNS is a free, global Domain Name System (DNS) resolution service, that one can use as an alternative to current DNS provider.
http://code.google.com/speed/public-dns/
Top Five Tips to Secure Website
A secure website is always essential ingredient of peace of mind for both web-master and the end user.These days hundreds of website come alive on the Internet because of high competition and >web hosting that comes with cheap price tag.But, what people do not understand is value of hack-proof website.Recently, according to a survey conducted by PricewaterhouseCoopers in the year 2009, companies are reducing their security related costs primarily due to recession.But, the number no. of victims is growing without any hurdle.This clearly indicates immense need for security.This post describes few most basic yet powerful ways to curb any hazard to your websites.
1)Vulnerability Assessment
A vulnerability scanner is a tool that searches and maps a system or network for different possible weakness and report it with feedback for the use of administrator.They can give you possible web application vulnerabilities like sql injection, XSS and firewall security breach.Nikto is a very useful open source scanner and also you can use Acunetix Web Vulnerability scanner.
2)Penetration Testing
This is part of security testing in which a deliberate and simulated attack is carried out to circumvent security of a system.This is a must to be deployed step for commercial websites.Security can not be full-proof, as secured wordpress web hosting can be compromised with c99 madshell script written in php.
3)Web Application Firewalls
Web application firewalls are essential for larger and advanced websites as these can not be affordable by everyone.These firewalls are specifically designed for fine tuning web application by keeping a check on HTTP traffic and data leakage by residing in between client and server.
4)Client Security Tools
A web-master can do everything from his part to secure a server.But, risk management has to be one of the most important priority.One can never predict about security in the future.So, clients have to advised by web-masters to use some of browser security tool to save themselves from any loss.Such a tool can be XSS me FireFox add on or Internet Explorer 8's in built XSS filter.
5)Application Whitelists
It is a policy that is employed by administrators to document congiguration pf applications put in the whitelist.This way they can detect any unauthorized changes to the server environment.
These are the five ways to put a secured website on the Internet.But, all these are not affordable by everyone.You must be aware of Internet mobs.While choosing a CMS for your website go for something that gets updated quickly with larger user base like Joomla, Nuke, drupal web hosting etc.
1)Vulnerability Assessment
A vulnerability scanner is a tool that searches and maps a system or network for different possible weakness and report it with feedback for the use of administrator.They can give you possible web application vulnerabilities like sql injection, XSS and firewall security breach.Nikto is a very useful open source scanner and also you can use Acunetix Web Vulnerability scanner.
2)Penetration Testing
This is part of security testing in which a deliberate and simulated attack is carried out to circumvent security of a system.This is a must to be deployed step for commercial websites.Security can not be full-proof, as secured wordpress web hosting can be compromised with c99 madshell script written in php.
3)Web Application Firewalls
Web application firewalls are essential for larger and advanced websites as these can not be affordable by everyone.These firewalls are specifically designed for fine tuning web application by keeping a check on HTTP traffic and data leakage by residing in between client and server.
4)Client Security Tools
A web-master can do everything from his part to secure a server.But, risk management has to be one of the most important priority.One can never predict about security in the future.So, clients have to advised by web-masters to use some of browser security tool to save themselves from any loss.Such a tool can be XSS me FireFox add on or Internet Explorer 8's in built XSS filter.
5)Application Whitelists
It is a policy that is employed by administrators to document congiguration pf applications put in the whitelist.This way they can detect any unauthorized changes to the server environment.
These are the five ways to put a secured website on the Internet.But, all these are not affordable by everyone.You must be aware of Internet mobs.While choosing a CMS for your website go for something that gets updated quickly with larger user base like Joomla, Nuke, drupal web hosting etc.
Monday, August 16, 2010
What is a drive-by download?
A drive-by download is a program that is automatically downloaded to your computer without your consent or even your knowledge. Unlike a pop-up download, which asks for assent (albeit in a calculated manner likely to lead to a "yes"), a drive-by download can be initiated by simply visiting a Web site or viewing an HTML e-mail message. If your computer's security settings are lax, it may be possible for drive-by downloads to occur without any further action on your part.
Frequently, a drive-by download is installed along with a user-requested application. (In this case, the unwanted application is sometimes called a barnacle.) For example, a file sharing program might include a spyware program that tracks and reports user information for targeted marketing purposes. An associated adware program can then generate pop-up advertisements using that information.
Xupiter, an Internet Explorer toolbar program, was frequently installed as a drive-by download in the early 2000s. The program replaced a user's home page, changed browser settings, and used a redirect to take all searches to the Xupiter Web site. In some versions, the program initiated drive-by downloads of other programs. Furthermore, although it came with an uninstall utility, Xupiter was quite challenging for the average computer user to remove.
Drive-by downloads continue to be a major security issue online. In April 2007, researchers at Google discovered hundreds of thousands of Web pages that initiated drive-by downloads. One in ten pages was found to be suspect. Sophos researchers in 2008 reported that they were discovering more than 6,000 new infected Web pages every day, or about one every 14 seconds. Many of these infections are connected to botnets, in which each PC is turned into a zombie that may then be directed to further malicious activity, like spam or DDoSWhat is a drive-by download? attacks.
Lock Your Desktop in Windows XP
If your computer is easily accessible by others and you do not wish for this to happen, you can easily lock it so that it is password protected. No one else will have access to it until you give them the required information. Here is how you do so.
Instructions
Things You'll Need:
- Windows XP
- Step 1Make sure you know the password to your computer.
- Step 2Press Ctrl+Alt+Del on your keyboard.
- Step 3Choose "Lock Desktop."
- Step 4Your computer will be locked immediately.
- Step 5If you need access to your desktop again, press Ctrl+Alt+Del.
- Step 6Enter your password and you will then be able to resume activity on the computer.
Sunday, August 15, 2010
Secretly Hide Any File Inside JPG Image File
Few months ago , USA Today story claimed that al-Qaeda operatives were sending out encrypted messages by hiding them inside digital photographs [jpg files] on eBay.
While the claim was never proved, it is very easy to hide [or embed] any other file[s] inside a JPEG image. You can place video clips, pdf, mp3, Office documents, zipped files, webpage or any other file format inside a JPEG image.
And when a suspecting user [read CIA, FBI] tries to open that jpeg file [with concealed information] in either a photo editing software or as a thumbnail inside Windows Explorer, it would be tough to make out if this camouflaged jpg file is different from any standard jpg image.
Let's say you want to hide a confidential PDF document from the tax investigation officers. What you can do is convert that file into a regular jpg image so even if anyone double-clicks this file, all he will see is a preview of the image and nothing else. And when you want to work on the actual PDF, just rename the extension from jpg to pdf.
Here's the full trick:
Step 1: You will need two files - the file you want to hide and one jpg image - it can be of any size or dimensions. [If you want to hide multiple files in one jpeg image, just zip them into one file]
Step 2: Copy the above two files to the C: folder and open the command prompt window.
Step 3: Move to the c: root by typing cd \ [if the files are in another folder, you'll have to change the prompt to that folder]
Step 4: The most important step - type the following command:
copy /b myimage.jpg + filetohide.pdf my_new_image.jpg
To recover the original PDF file, just rename my_new_image.jpg to filename.pdf.
Here we illustrated with an pdf file as that works with simple renaming. If you want to apply this technique to other file formats like XLS, DOC, PPT, AVI, WMV, WAV, SWF, etc, you may have to first compress them in RAR format before executing the copy /b DOS command.
To restore the original file, rename the .jpg file to .rar and extract it using 7-zip or Winrar.
Stupid Command Prompt Tricks
Windows XP isn't known for its powerful command line interface. Still, one of the first things I do on any fresh Windows install is set up the "Open Command Window Here" right click menu. And hoary old cmd.exe does have a few tricks up its sleeve that you may not know about.

The first thing you'll want to do is Start, Run, cmd.exe, then right click the window menu and choose properties. Be sure to enable the following quality of life improvements:
And of course, set the font and colors to taste. I use green-screen style colors (background 0 55 0, foreground 0 255 0) with Lucida Console as pictured above. But if you prefer Comic Sans here, be my guest! When exiting this dialog, you'll be prompted to save. Make sure you select "Save properties for future windows with same title" so all future command prompts will benefit from these improved settings.
There are also a few helpful keyboard shortcuts that aren't always widely known:
The first thing you'll want to do is Start, Run, cmd.exe, then right click the window menu and choose properties. Be sure to enable the following quality of life improvements:
- Options | Command History | Buffer Size | 500
- Options | Command History | Discard Old Duplicates | True
- Options | Edit Options | QuickEdit Mode | True
- Layout | Screen buffer size | Height | 999
- Layout | Window size | Height | 50
And of course, set the font and colors to taste. I use green-screen style colors (background 0 55 0, foreground 0 255 0) with Lucida Console as pictured above. But if you prefer Comic Sans here, be my guest! When exiting this dialog, you'll be prompted to save. Make sure you select "Save properties for future windows with same title" so all future command prompts will benefit from these improved settings.
There are also a few helpful keyboard shortcuts that aren't always widely known:
- Pressing arrow up selects a previous command from your command history; similarly, arrow down selects the next command.
- Pressing F7 pops up your command history list.
- You can drag n' drop files or folders from an explorer window into a command prompt; this inserts the quoted path as if you had manually pasted it.
- Tab completion is fully supported; type edit *.ini then hit TAB to iterate through all matches. Use SHIFT+TAB to move to the previous match. This works for partial filenames as you would expect, and in all commands.
- Tired of the typical "c:\windows\system32\cmd.exe" window title? Change it using the TITLE command.
- ALT+ENTER takes your command prompt to fullscreen mode and back again.
Some Command Prompt Tricks
Last night i was cleaning Junk from my PC. Because .. I test lots of freewares to find out best freeware programs for my needs. Then i found found some Command Prompt tricks i collected few years ago. This trick are Old but still.. If you want to have some fun with command prompt , here is some…
Watch A Movie Created with Command Prompt
 Command prompts movie..!! amazing Creation. But you need active internet connection to enjoy this movie. It’s a star wars movie. Here is how to watch this movie :
Command prompts movie..!! amazing Creation. But you need active internet connection to enjoy this movie. It’s a star wars movie. Here is how to watch this movie :
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
And hit Enter. Now enjoy the Star wars Movie.
Shutdown PC On your LAN Network
 This trick will shutdown a selected pc from Your LAN network. You can apply this trick in your office or school.. but i take no responsibilities fro any action. Its just for fun. Here is how to use this trick :
This trick will shutdown a selected pc from Your LAN network. You can apply this trick in your office or school.. but i take no responsibilities fro any action. Its just for fun. Here is how to use this trick :
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
And hit Enter. You will see remote shutdown Window. If you know someone’s IP on a computer in your Local Area network, type in their IP Address after clicking the add button.
3. After entering the IP Address click OK . Now watch the person’s face as their computer shuts down.
Some users have asked me that they got Access Denied error for remote shutdown. Add the user with the privilege to force a remote shutdown on the computer you are about to Shutdown.To do this go to control panel > Administrative Tools > Local Security Settings. Now go to Security Settings > Local Policies > User Rights Assignment. Double-click on Force shutdown from a remote system in the right pane and Click on Add User or Group. Add the computer that runs the remote shutdown command.
Or you can do this go the computer you are about to Shutdown
a) Go to Start > Run > type in Regedit in the dialog box and hit enter
b) Go to My Computer/HKEY_LOCAL_MACHINE /system/currentcontrolset/control/lsa
c) Find “forceguest” in the right pane Double click on it to modify This entry change the value from “1″ entry to “0″
Some Other Fun on Command Prompt
At first start command prompt from Start > Run, the type in cmd click on OK and enter the following command:
Here your Custom Message indicates any message. Then hit Enter check out the title bar of
the command window. Just a cheap little trick…
Here is another.. Run command prompt and type in
For example if you type prompt hello your c: prompt will change to hello
That’s all for now Have fun and enjoy..
Watch A Movie Created with Command Prompt

STAR WARS MOVIE
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
telnet towel.blinkenlights.nlAnd hit Enter. Now enjoy the Star wars Movie.
Shutdown PC On your LAN Network

Remote Shutdown
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
shutdown.exe -iAnd hit Enter. You will see remote shutdown Window. If you know someone’s IP on a computer in your Local Area network, type in their IP Address after clicking the add button.
3. After entering the IP Address click OK . Now watch the person’s face as their computer shuts down.
Some users have asked me that they got Access Denied error for remote shutdown. Add the user with the privilege to force a remote shutdown on the computer you are about to Shutdown.To do this go to control panel > Administrative Tools > Local Security Settings. Now go to Security Settings > Local Policies > User Rights Assignment. Double-click on Force shutdown from a remote system in the right pane and Click on Add User or Group. Add the computer that runs the remote shutdown command.
Or you can do this go the computer you are about to Shutdown
a) Go to Start > Run > type in Regedit in the dialog box and hit enter
b) Go to My Computer/HKEY_LOCAL_MACHINE /system/currentcontrolset/control/lsa
c) Find “forceguest” in the right pane Double click on it to modify This entry change the value from “1″ entry to “0″
Some Other Fun on Command Prompt
At first start command prompt from Start > Run, the type in cmd click on OK and enter the following command:
title your Custom MessageHere your Custom Message indicates any message. Then hit Enter check out the title bar of
the command window. Just a cheap little trick…
Here is another.. Run command prompt and type in
prompt whatever you want it sayFor example if you type prompt hello your c: prompt will change to hello
That’s all for now Have fun and enjoy..
Tags for the article:
- command prompt tricks,command prompt hacks,cool command prompt tricks,cmd commands tricks,cmd prompt tricks,cmd tricks,command prompt tricks and hacks,cool cmd commands,Command promt tricks,command prompt trick
Microsoft crazy fact
An unbelievable problem in microsoft ...At Microsoft the whole Team, including Bill Gates, couldn't answer why this happened!
It was discovered by a Brazilian. Try it out yourself... Open Microsoft Word and type =rand (200, 99) And then press ENTER then see the magic..........
Create Cmd Prompt When Your Command Prompt Does Not Works
Hi frds A trick to create command prompt some times run is disabled in your pc due to virus so create ur cmd prompt and continue ur works as usual PASTE THIS CODE IN A NOTE PAD @echo off cmd @echo on AND SAVE THE NOTEPAD as cmd.bat cmd.bat is the name u r going to save
Saturday, August 14, 2010
A Funny Trick In Windows Xp
HI frds a funny trick in windows XP Try our this u can c star wars in windows XP
its really nice try out dis friends
GO TO start>run.......
TYPE telnet towel.blinkenlights.nl
hit enter....and then Check it out please comment if u like it
A Trick To Shutdown Ur Pc Or Ur Friends Pc
1. Right click on desktop>select New>shortcut
2. In the shortcut window type : shutdown -s -t 60 -c
"the message you want to display"
3. Select Next
4. Name it anything. Now, double click it ! Scared ??? Nothing happened ! Remedy : 1. Go to start>Run 2. Type : shutdown -a 3. Hit Enter
A Bunch Of Cool Tips And Tricks
Windows Logon Box; Wanna Rename It
Run regedit and go to HKEY_Local_Machine\Software\Microsoft \Windows\CurrentVersion\Winlogon
Then add or change the key:
LegalNoticeCaption REG_SZ="(Title for Box)"
And the same for this key:
LegalNoticeText REG_SZ="(Message to be displayed in the box)"
Wanna Move Your Start Button
How to move or close the start button!
1. Click on the Start button.
2. Press the Esc key.
3. Press the Alt and the - or dash keys at the same time.
4. This will give you a menu, you can move or close.
5. But if you move it you need to use the arrow keys and not the mouse.
6. When you get it where you want it, push the Enter button.
How to Change the Name of the Start Menu Button
To rename the start button, you will need a hex editor.
My preference is UltraEdit
Copy the \windows\explore.exe file to a new name (e.g. explorer_1.exe)
With the hex editor, open that file and go to offset 412b6
You will see the word start with blanks between each letter
Edit it be any 5 characters or less
Save the file
Boot to DOS
Copy the existing c:\windows\explorer.exe to explorer.org
Copy explorer_1.exe to explorer.exe
You will also need to replace the explorer.exe in the c:\windows\system32\dllcache file as well with the new one.
Note: If the partition is NTFS and you can't access the files from DOS:
Start Regedit
Go to HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon.
Change the value of Shell from Explorer.exe to explorer_1.exe
My preference is UltraEdit
Copy the \windows\explore.exe file to a new name (e.g. explorer_1.exe)
With the hex editor, open that file and go to offset 412b6
You will see the word start with blanks between each letter
Edit it be any 5 characters or less
Save the file
Boot to DOS
Copy the existing c:\windows\explorer.exe to explorer.org
Copy explorer_1.exe to explorer.exe
You will also need to replace the explorer.exe in the c:\windows\system32\dllcache file as well with the new one.
Note: If the partition is NTFS and you can't access the files from DOS:
Start Regedit
Go to HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon.
Change the value of Shell from Explorer.exe to explorer_1.exe
Hidden Music In Win Xp.....
To hear this sound, first of all go to Folder Options and underthe "View" tab,check "Show hidden files and folder" and uncheck"Hide protected system files". Now navigate to the drive where Windows XP is installed.So if C:\is the drive where Windows XP is installed, goto C:\WINDOWS\system32\oobe\images There you will find a file Title.wma.Open in with media playernd listen to it.
How To Close All Windows Programs Quickly
How to Close All Windows Programs quickly?
A cool tip to minimize and maximize all your active windows
programs. You can do all using your mouse, but if you want to do this with keyboard then simply press Windows key+M to minimize all active programs and later maximize it using Windows key+Shift+M.
If you want to minimize the all active windows programs one by one then use the shortcut by pressing Alt+Space+N keys and sequentially maximize the active windows programs using shortcut Alt+Space+X keys.
Automatic Mouse Moving Program
1. SlaveMouse : Automatic Mouse moving and clicking
SlaveMouse is a program that makes your mouse move and click automatically on locations that you defined. It is also possible to write text on defined locations.Click here to learn more about SlaveMouse.
Screenshot
2. SelfMouse : Automatic Mouse moving and clicking
SelfMouse is a simple program that makes your mouse move and click automatically on locations that you defined.Click here to learn more about SelfMouse.
Screenshot
3. MacroMouse: Program the mouse yourself for Automatic Mouse moving and clicking
MacroMouse is a tool that lets you program your mouse-pointer by using some simple instructions. It provides a simple programming language which can be understood by MacroMouse and makes your mouse do what you want over and over again.Click here to learn more about MacroMouse.
Screenshot
4. ClickAlive : Keep your connection online
ClickAlive is a simple program that makes your mouse move and click automatically on a location after the mouse has been idle for a specified time. Click here to learn more about ClickAlive.Screenshot
How To Move Your Mouse Cursor Without Mouse
How to move your mouse cursor without mouse?
You can control your mouse pointer with keyboard keys in allwindows versions.
When your mouse stops working, you can enable this keyboardfeature to complete your
important work. This keyboard mouse can performs all taskssame like a normal mouse. Follow the given steps to activate the keyboard mouse: To edit this feature, first you should log onto your computerwith administrative rights. To activate this feature, press Alt+Shift+NumLock keys at onceand you will receive a small MouseKey box. To keep MouseKeys on, click on Ok button or click on cancelbutton to cancel MouseKeys box. Click on Settings button, if you want to adjust the mousecursor detail settings. Here a new dialog box will appear with the title "Settingsfor MouseKeys", now you can manage all mouse settings
for example mouse cursor speed, acceleration and some otherfeatures. Now using Numeric keypad, you can move your mouse pointer. Thecontrols are: 1,2,3,4,6,7,8 and 9 keys are used to move the mouse cursorinto different directions. Key 5 is used as mouse click button. Insert key used to hold down mouse button. + Sign used to double click on any object. Delete button used to release the mouse. Click on NumLock button to disable this keyboard mouse feature
Magic XP
Well i was just thinking that a lot of odd stuff happens on the pc's u know....
it's not dangerous but still is fun to do...
Try these for some fun:-)
MAGIC #1
An Indian discovered that nobody can create a FOLDER anywhere on the computer which can be named as "CON". This is something pretty cool...and unbelievable. .. At Microsoft the whole Team, couldn't answer why this happened! Can you create a folder named “con”, “prn”, “nul” “com1″ “com2″ “lpt1″ etc.
in windows ?The answer is NO and YES!
NO because when create a new folder and try to rename it to any one of the above specified names, you know what happens! In Windows XP the folder name automatically changes back to “New Folder” no matter you try any number of times. Where as in Windows Vista/7 when you try to rename the file you get an error message “The specified device name is invalid”.
What is the reason for this? Simple, these names represent the internal devices and hence we cannot create folders with the above names.
YES because it is still possible to create these folders using the command prompt. Here’s the instructions to create it.
1. Go to command prompt
2. Type in prompt (FOR EG. TO CREATE CON FOLDER IN E: DRIVE)
C:\>md \\.\e:\con
NOTE: “con” can be replaced by any other names such as “prn”, “nul” “com1″ “com2″ “lpt1″ etc.
3. To delete the folder use the following commandC:\>rd \\.\e:\con
NOTE: The folder can only be deleted from the command prompt.You cannot remove it by right-click delete.
Friday, August 13, 2010
The Indian Language Converter for HTML Pages
- Akhila Bharathan (அகிலா பரதன்), inspiration and dedicated to.
- Vidya Sumankar (பல் மருத்துவர் வித்யா சுமன்கர்) - language coordinator.
- Vijay Lakshminarayanan (விஜய் லக்ஷ்மிநாராயணன்) - idea, design, coding, testing.
- Prathap Parameswaran (பிரதாப் பரமேஸ்வரன்) (പ്രതാപ് പരമേശ്വരന്) - language consultant, Tamil (தமிழ்) and Malayalam (മലയാളം).
- Sumanth Naropanth - language consultant, Kannada (ಕನ್ನಡ) and testing.
- Bharat Thyagarajan (भरत त्यागराजन) - language consultant, Hindi (हिन्दी).
- Yash Gadhiya (યશ ગઢિયા) - language consultant and maintainer, Gujarati (ગુજરાતી).
http://www.yash.info/
Google Docs
You can upload files from your desktop or create documents, spreadsheets, forms, and presentations right in Google Docs.
The result? You can open all these files anywhere and share them with anyone.
Here's what you can do with documents:
- Upload and convert Word documents, OpenOffice, RTF, HTML, text (.txt), Open Office (.odt), and StarOffice Writer (.sxw) files (or create documents from scratch).
- Easily format your documents, spell-check them, etc.
- Invite others by email to edit or view your documents.
- Edit documents online with whomever you choose.
- View your documents' revision history and roll back to any version.
- Publish documents online to the world, as webpages or post documents to your blog.
- Download documents to your desktop as Word, OpenOffice, RTF, PDF, HTML or zip.
- Email your documents out as attachments.
Here's what you can do with spreadsheets:
- Import and convert .xls, .csv, .txt and .ods formatted data.
- Export .xls, .csv, .txt and .ods formatted data and PDF and HTML files.
- Use formatting and formula editing so you can calculate results and make your data look the way you want it.
- Chat in real time with others who are editing your spreadsheet.
- Embed a spreadsheet, or individual sheets of your spreadsheet, in your blog or website.
Here's what you can do with presentations:
- Share and edit presentations with your friends and coworkers.
- Import and convert existing presentations in .ppt and .pps file types.
- Download your presentations as a PDF, a PPT, or a TXT file.
- Easily edit your presentations.
- Insert images and videos, and format your slides to fit your preferences.
- Allow real-time viewing of presentations, online, from separate remote locations.
- Publish and embed your presentations in a website, allowing access to a wide audience.
FUNNY PC TRICKS
For those of you using Windows, do the following:
1. Open an empty notepad file
2. Type "Bush hid the facts" (without the quotes)
3. Save it as whatever you want.
4. Close it, and re-open it.
Is it just a really weird bug? :-?? Any string of characters with four letters, three letters, three
letters, five letters (4,3,3,5) will produce the same results. It's a
Notepad bug. Some other examples of this 4,3,3,5 bug are:
"Bill fed the goats"
"hhhh hhh hhh hhhhh"
Notepad2 exhibits the same behavior because the bug isn't in Notepad
itself, but rather in a Windows programming function called:
"IsTextUnicode".
General Interesting Facts
| General Interesting Facts - New amazing facts are routinely added randomly to the list!
|
How To Wipe A Hard Drive

Why Erase Hard Drives?
An index of files is maintained on every hard drive, this index tells the drive where information is stored. When you install/save a file, it is often scattered across the drive in different locations. When you command your computer to open a file the hard drive consults the index, before gathering the pieces and reconstructing them into a whole. When you choose to delete/uninstall a file the links between the files and the index disappear, meaning that your drive no longer knows where to find it. This tells your computer that the file is no longer required and that the relevant space on your hard drive can be overwritten. This deleted file actually remains in the drive until it is overwritten, which unless you completely fill your drive will probably never happen. Even a file that has been overwritten can be recovered by somebody that really knows their stuff. If for example you were planning on selling your computer, and just deleted everything, it is likely that much of this information still exists for anybody with a shareware program to find. I cannot emphasise enough just how important it is to wipe your drives no matter what you are going to do with it, even those that are giving a computer to their dear old auntie Sophie; you don't know whether Sophie will throw that computer away in a years time, ready for pickings by the local fraudsters.
Reformat The Hard Drive
Reformatting a hard drive prepares it for a complete installation or reinstallation of an operating system, and that is your goal. All versions of Windows prior to Windows XP allow you to create a start-up disk, you need this to reformat your drive. You can do this by:-
Start > Settings > Control Panel. Click 'Add/Remove Programs', then 'Start-up Disk', then 'Create Disk'. Then follow instructions to burn your start up disk.
On Windows XP you have to download this start-up disk info, you can do this by visiting www.bootdisk.com and clicking on 'DOS - Windows 9X/NT4/2000/XP Excellent Bootdisks', download the Windows XP Custom Install Disk and save it to either CD or Floppy. Then restart your system with the floppy/disk in the drive and follow on screen instructions (this is easy).
For Windows Vista, you should have an operating system disk. If you do, you just need to insert this, reboot your computer, and follow the instructions. This should reformat your drive in the process (they have made these things a lot easier). If for some reason you haven't got an operating disk, then sorry, you will have to either a) buy another one, or b) do whatever it was you did to get your operating system in the first place ;)
Start > Settings > Control Panel. Click 'Add/Remove Programs', then 'Start-up Disk', then 'Create Disk'. Then follow instructions to burn your start up disk.
On Windows XP you have to download this start-up disk info, you can do this by visiting www.bootdisk.com and clicking on 'DOS - Windows 9X/NT4/2000/XP Excellent Bootdisks', download the Windows XP Custom Install Disk and save it to either CD or Floppy. Then restart your system with the floppy/disk in the drive and follow on screen instructions (this is easy).
For Windows Vista, you should have an operating system disk. If you do, you just need to insert this, reboot your computer, and follow the instructions. This should reformat your drive in the process (they have made these things a lot easier). If for some reason you haven't got an operating disk, then sorry, you will have to either a) buy another one, or b) do whatever it was you did to get your operating system in the first place ;)
Alternatively, Buy Software
If you don't know much about computers, or just want to make sure that you get it write, there are some fantastically effective software's out there. They guarantee that your files cannot be found after the software has finished filling your disk space with complete nonsense. And this could be the safest route for anybody that is giving their computer away, once such program is Norton SystemWorks which includes an excellent application called 'Wipe Info' which is considered in industry as fail safe. Another is DataEraser by OnTrack, which has an equally excellent reputation. Although there are thousands of applications that claim to offer the same quality service, please be careful to buy the software of a solid and established brand. These software's do take a while though, normally long enough to justify leaving it running overnight!
Related Hubs
Although It Can Be Fun Destroying Hard Drives
If your information is really that sensitive, or you are just that damn paranoid, or you are throwing your computer away anyway....... then there really is just one option. And that is DESTRUCTION!!! To do this you need to:-
1. Unplug the wires on the hard drive and remove the screws, slide the hard drive out.
2. Then read my forthcoming hub '5 Great Ways To Destroy Hard Drive Data'
1. Unplug the wires on the hard drive and remove the screws, slide the hard drive out.
2. Then read my forthcoming hub '5 Great Ways To Destroy Hard Drive Data'
funny computer tricks
1. lets start with a funny one. just copy the below code and paste it to your web browser address bar and press enter..
javascript:function Shw(n) {if (self.moveBy) {for (i = 35; i > 0; i--) {for (j = n; j > 0; j--) {self.moveBy(1,i);self.moveBy(i,0);self.moveBy(0,-i);self.moveBy(-i,0); } } }} Shw(6)
we will see that your browser is shaking :))
2. do you know how to make a folder without a name? is it possible? oh yea it is possible. just try it out..
#clcik the folder.. right click on it..then click rename...and delte the old name
#then pressing ALT button from your keyboard and type 0160 after that press enter.
important think to notice :(you have to type by pressing the ALT button ..don't stop pressing and while you will type 0160 it will not appear..u will continue typing and press enter.. thats it)
3. now i am gonna show you how to make your pc faster than before. i can make your pc about 200% faster. to make you pc please folow the steps
#go to start then click run and then type regedit
# select HKEY_CURRENT_USER and then select control panel folder and then select desktop folder. do it correctly
# you will see registry setting at your right hand side after that select menu show delay and then right click and select modify.
# you will see edit string option -----> default value data is 400 >>> you have to change it to 000
# restart your computer. you will see your computer is much more faster
4. you can test your anti virus is it working or not. just follow my instruction
# open a wordpad or not pad and save this.
X50!P%@AP[4\PZX54(P^)7CC)7}EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
save it as eicar.com . while doing this your anti-virus should stop you. its not harmful either but if the anti virus is active it will warn you. if it does not then your anti virus is good for nothing .
ohh i am so tired. i cant write more..feeling very sleepy ZzZZzZzZ .. i hope my hub will help you for getting some interest fact. please do comment
javascript:function Shw(n) {if (self.moveBy) {for (i = 35; i > 0; i--) {for (j = n; j > 0; j--) {self.moveBy(1,i);self.moveBy(i,0);self.moveBy(0,-i);self.moveBy(-i,0); } } }} Shw(6)
we will see that your browser is shaking :))
2. do you know how to make a folder without a name? is it possible? oh yea it is possible. just try it out..
#clcik the folder.. right click on it..then click rename...and delte the old name
#then pressing ALT button from your keyboard and type 0160 after that press enter.
important think to notice :(you have to type by pressing the ALT button ..don't stop pressing and while you will type 0160 it will not appear..u will continue typing and press enter.. thats it)
3. now i am gonna show you how to make your pc faster than before. i can make your pc about 200% faster. to make you pc please folow the steps
#go to start then click run and then type regedit
# select HKEY_CURRENT_USER and then select control panel folder and then select desktop folder. do it correctly
# you will see registry setting at your right hand side after that select menu show delay and then right click and select modify.
# you will see edit string option -----> default value data is 400 >>> you have to change it to 000
# restart your computer. you will see your computer is much more faster
4. you can test your anti virus is it working or not. just follow my instruction
# open a wordpad or not pad and save this.
X50!P%@AP[4\PZX54(P^)7CC)7}EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
save it as eicar.com . while doing this your anti-virus should stop you. its not harmful either but if the anti virus is active it will warn you. if it does not then your anti virus is good for nothing .
ohh i am so tired. i cant write more..feeling very sleepy ZzZZzZzZ .. i hope my hub will help you for getting some interest fact. please do comment

Download Internet Explorer 8
Internet Explorer 8 is the latest version of the familiar web browser you are most comfortable using, helping you get everything you want from the web faster, easier, more privately and securely than ever before.
Faster:
Internet Explorer 8 is more responsive with new pages and tabs, opening up fast and reliably. You can now get to the information you care about most, in fewer steps; one click access to your webmail, favorite news sites or other online services.
Easier:
Reduce the steps to accomplish many common tasks, and automate your access to real time information updates. You can keep track of your favorite sports team, news, weather with a single click.
More Private:
Helps protect your privacy and confidential information where ever you go on the web.
More Secure:
Helps protect and stop malicious software from reaching your PC, and makes it easier to detect when a website is an imposter.
* Download Internet Explorer 8 for Windows XP
* Download Internet Explorer 8 for Windows Vista
Keyboard shortcuts for Windows
Windows system key combinations
- F1: Help
- CTRL+ESC: Open Start menu
- ALT+TAB: Switch between open programs
- ALT+F4: Quit program
- SHIFT+DELETE: Delete item permanently
- Windows Logo+L: Lock the computer (without using CTRL+ALT+DELETE)
Windows program key combinations
- CTRL+C: Copy
- CTRL+X: Cut
- CTRL+V: Paste
- CTRL+Z: Undo
- CTRL+B: Bold
- CTRL+U: Underline
- CTRL+I: Italic
Mouse click/keyboard modifier combinations for shell objects
- SHIFT+right click: Displays a shortcut menu containing alternative commands
- SHIFT+double click: Runs the alternate default command (the second item on the menu)
- ALT+double click: Displays properties
- SHIFT+DELETE: Deletes an item immediately without placing it in the Recycle Bin
General keyboard-only commands
- F1: Starts Windows Help
- F10: Activates menu bar options
- SHIFT+F10 Opens a shortcut menu for the selected item (this is the same as right-clicking an object
- CTRL+ESC: Opens the Start menu (use the ARROW keys to select an item)
- CTRL+ESC or ESC: Selects the Start button (press TAB to select the taskbar, or press SHIFT+F10 for a context menu)
- CTRL+SHIFT+ESC: Opens Windows Task Manager
- ALT+DOWN ARROW: Opens a drop-down list box
- ALT+TAB: Switch to another running program (hold down the ALT key and then press the TAB key to view the task-switching window)
- SHIFT: Press and hold down the SHIFT key while you insert a CD-ROM to bypass the automatic-run feature
- ALT+SPACE: Displays the main window's System menu (from the System menu, you can restore, move, resize, minimize, maximize, or close the window)
- ALT+- (ALT+hyphen): Displays the Multiple Document Interface (MDI) child window's System menu (from the MDI child window's System menu, you can restore, move, resize, minimize, maximize, or close the child window)
- CTRL+TAB: Switch to the next child window of a Multiple Document Interface (MDI) program
- ALT+underlined letter in menu: Opens the menu
- ALT+F4: Closes the current window
- CTRL+F4: Closes the current Multiple Document Interface (MDI) window
- ALT+F6: Switch between multiple windows in the same program (for example, when the Notepad Find dialog box is displayed, ALT+F6 switches between the Find dialog box and the main Notepad window)
Shell objects and general folder/Windows Explorer shortcuts
For a selected object:- F2: Rename object
- F3: Find all files
- CTRL+X: Cut
- CTRL+C: Copy
- CTRL+V: Paste
- SHIFT+DELETE: Delete selection immediately, without moving the item to the Recycle Bin
- ALT+ENTER: Open the properties for the selected object
To copy a file
Press and hold down the CTRL key while you drag the file to another folder.To create a shortcut
Press and hold down CTRL+SHIFT while you drag a file to the desktop or a folder.General folder/shortcut control
- F4: Selects the Go To A Different Folder box and moves down the entries in the box (if the toolbar is active in Windows Explorer)
- F5: Refreshes the current window.
- F6: Moves among panes in Windows Explorer
- CTRL+G: Opens the Go To Folder tool (in Windows 95 Windows Explorer only)
- CTRL+Z: Undo the last command
- CTRL+A: Select all the items in the current window
- BACKSPACE: Switch to the parent folder
- SHIFT+click+Close button: For folders, close the current folder plus all parent folders
Windows Explorer tree control
- Numeric Keypad *: Expands everything under the current selection
- Numeric Keypad +: Expands the current selection
- Numeric Keypad -: Collapses the current selection.
- RIGHT ARROW: Expands the current selection if it is not expanded, otherwise goes to the first child
- LEFT ARROW: Collapses the current selection if it is expanded, otherwise goes to the parent
Properties control
- CTRL+TAB/CTRL+SHIFT+TAB: Move through the property tabs
Accessibility shortcuts
- Press SHIFT five times: Toggles StickyKeys on and off
- Press down and hold the right SHIFT key for eight seconds: Toggles FilterKeys on and off
- Press down and hold the NUM LOCK key for five seconds: Toggles ToggleKeys on and off
- Left ALT+left SHIFT+NUM LOCK: Toggles MouseKeys on and off
- Left ALT+left SHIFT+PRINT SCREEN: Toggles high contrast on and off
Microsoft Natural Keyboard keys
- Windows Logo: Start menu
- Windows Logo+R: Run dialog box
- Windows Logo+M: Minimize all
- SHIFT+Windows Logo+M: Undo minimize all
- Windows Logo+F1: Help
- Windows Logo+E: Windows Explorer
- Windows Logo+F: Find files or folders
- Windows Logo+D: Minimizes all open windows and displays the desktop
- CTRL+Windows Logo+F: Find computer
- CTRL+Windows Logo+TAB: Moves focus from Start, to the Quick Launch toolbar, to the system tray (use RIGHT ARROW or LEFT ARROW to move focus to items on the Quick Launch toolbar and the system tray)
- Windows Logo+TAB: Cycle through taskbar buttons
- Windows Logo+Break: System Properties dialog box
- Application key: Displays a shortcut menu for the selected item
Microsoft Natural Keyboard with IntelliType software installed
- Windows Logo+L: Log off Windows
- Windows Logo+P: Starts Print Manager
- Windows Logo+C: Opens Control Panel
- Windows Logo+V: Starts Clipboard
- Windows Logo+K: Opens Keyboard Properties dialog box
- Windows Logo+I: Opens Mouse Properties dialog box
- Windows Logo+A: Starts Accessibility Options (if installed)
- Windows Logo+SPACEBAR: Displays the list of Microsoft IntelliType shortcut keys
- Windows Logo+S: Toggles CAPS LOCK on and off
Dialog box keyboard commands
- TAB: Move to the next control in the dialog box
- SHIFT+TAB: Move to the previous control in the dialog box
- SPACEBAR: If the current control is a button, this clicks the button. If the current control is a check box, this toggles the check box. If the current control is an option, this selects the option.
- ENTER: Equivalent to clicking the selected button (the button with the outline)
- ESC: Equivalent to clicking the Cancel button
- ALT+underlined letter in dialog box item: Move to the corresponding item
Note This is a "FAST PUBLISH" article created directly from within the Microsoft support organization. The information contained herein is provided as-is in response to emerging issues. As a result of the speed in making it available, the materials may include typographical errors and may be revised at any time without notice.
APPLIES TO
- Windows Server 2008 Datacenter
- Windows Server 2008 Enterprise
- Windows Server 2008 Standard
- Microsoft Windows Server 2003, Datacenter Edition (32-bit x86)
- Microsoft Windows Server 2003, Enterprise x64 Edition
- Microsoft Windows Server 2003, Enterprise Edition (32-bit x86)
- Microsoft Windows Server 2003, Enterprise Edition for Itanium-based Systems
- Microsoft Windows Server 2003, Standard x64 Edition
- Microsoft Windows Server 2003, Standard Edition (32-bit x86)
- Microsoft Windows 2000 Server
- Microsoft Windows 95
- Windows Vista Business
- Windows Vista Enterprise
- Windows Vista Home Basic
- Windows Vista Home Premium
- Windows Vista Starter
- Windows Vista Ultimate
- Microsoft Windows XP Home Edition
- Microsoft Windows XP Professional
- Microsoft Windows XP Starter Edition
- Microsoft Windows XP Tablet PC Edition
Keywords: | kbpubtypekc kbenablemove kbenablesight kbenv kbfaq kbinfo KB126449 |
Download Hindi Mp3
Download Hindi Mp3 music Music for free, Hindi remixes, pop, movies, film songs in mp3 format.
- Hindi Mp3 music
- Hindi remixes
- film songs in mp3 format
- Bollywood Movies
- Lyrics
- Translations
Thursday, August 12, 2010
Free Online Antivirus Scanners
If you suspect that your computer might have a virus and you can still access the web, you can use a free online antivirus scanner to identify and eliminate any viruses that have infected your computer. An online antivirus scanner will not be as fast as an antivirus utility that is installed on your computer. An installed antivirus utility can stay active at all times and scan files as you open them. But if you don't have an installed antivirus utility, or if you let your subscription expire, an online antivirus scanner may be your only choice.
To use an online antivirus scanner, you'll need Internet Explorer version 5.0 or higher installed on your computer. In fact, one way you can avoid getting a virus in the first place is to update your browser to the latest version. You should also make sure you have all the latest updates from Microsoft's Windows Update website.
Note: In my experience, Microsoft's update site doesn't work too well with a dial-up connection. They have the bandwidth is pinched off tight and it stalls frequently.
The first time you use an online antivirus scanner website you'll be required to download an ActiveX control. Make sure your browser is configured to accept ActiveX controls.
Symantec Security Response
Click on the "Check for security risks" icon, then click on the "Virus Detection" link. Symantec also provides a "Security Scan", which checks whether your computer is configured to be safe from hackers, viruses, and other attacks.
Trend Micro
This Tokyo company has been in the online antivirus scanner business longer than anyone else. Click on the "Personal" tab (unless you're an Enterprise). Under the heading "VIRUS ALERT", click on the link "Free Online Scan".
Panda Software
Panda Software is another company that's been in the antivirus business for a long time with computer installed utilities. Click on "Online virus check" or on the Panda ActiveScan icon. A new browser window will open with Panda ActiveScan.
RAV AntiVirus
This company's antivirus technology was acquired by Microsoft in 2003. Click on "Scan online" in the menu on the left side. The first time you use RAV AntiVirus you must download and install over 1MB of required files. On subsequent visits to the site, only the updated files (up to 100Kb, depending on how often you use the service) will need to be downloaded.
Bitdefender
This Bucharest, ROMANIA based company has Macromedia Flash on every page. If you use dial-up, that will probably bog down your connection enough to make this site useless. Do they think someone who is seeking antivirus scanning would want to download Macromedia Flash player? Macromedia Flash is used by bored webpage designers who have a lot of time on their hands and a lot of money to waste. Unless no other online antivirus scanner works for you, I would recommend avoiding this site until they lose the Flash.
Troubleshoot Windows XP with Event Viewer
Anything noteworthy that happens in Windows is referred to as an "event" and is recorded in an "event log". Windows actually creates three logs, the Application log stores events related to applications. The Security log stores events related to security related events, for example user logons. The System log stores Windows operating system events. Most people ignore these logs; however, they can be very useful for troubleshooting purposes.
- Some applications create their own separate event log which is displayed in Event Viewer along with Windows standard Application, Security and System event logs. Sometimes an aplication will leave its event log behind after you uninstall it. You can remove the log by removing its subkey from the key:
\Windows\system32\config
It will have an .evt extension. But never remove AppEvent.evt, SecEvent.evt, or SysEvent.evt, the Application, Security and System event logs.
To view an event log, in Control Panel select the Administrative Tools. In the Administrative Tools window, select the Event Viewer. You can also open Event Viewer by selecting Start | Run and typing eventvwr.msc in the Run dialog box.
 There are three types of events, an Information event records that a task was performed successfully or that a service had a change of status. Information events are usually nothing to be concerned about. A Warning event records that a noncritical error occurred. If your system is recording a high number of Warning events from a single source, you might want to investigate the cause.
There are three types of events, an Information event records that a task was performed successfully or that a service had a change of status. Information events are usually nothing to be concerned about. A Warning event records that a noncritical error occurred. If your system is recording a high number of Warning events from a single source, you might want to investigate the cause.
An Error event records that a critical error has occurred. You might want to investigate an Error event before it becomes a more serious problem. To view the details of an event, double-click on the event in the list. The Event Properties dialog box will open. The Event Properties dialog box Description section will display a description of the event, and maybe a link to a source of more information about that type of event.
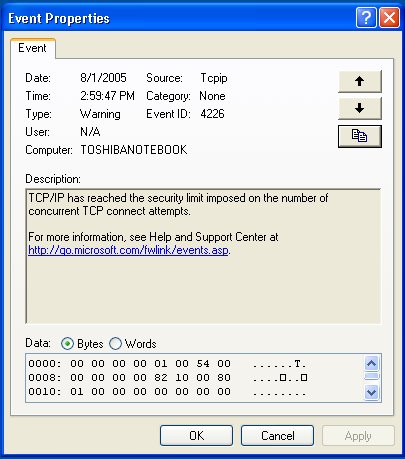
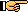 Note the memory dump data at the bottom of the dialog box. This information would only be useful to Microsoft's programmers in India.
Note the memory dump data at the bottom of the dialog box. This information would only be useful to Microsoft's programmers in India.
How to Use Event Description Information
The information provided by the Event Properties dialog box should point you towards the source of the problem. Use your regular troubleshooting tools, resources, and techniques to solve the problem.
If the Event Properties dialog box includes a link to Micosoft's website (and your computer is connected to the Internet), click on the link. This will execute the Microsoft Help and Support Center which will retrieve information related to the error from Microsoft's web site. This information may include instructions about how to solve the problem, along with links to relevant information on Microsoft's web site.
You can also visit the Microsoft Knowledge Base where you can search for information by typing the error description or a question into the search box. You can also type the error description into a general search engine to perform a general web search.
When to Use Event Viewer
Use the Event Viewer when an error occurs while using your computer. Windows will generate an Error event log proving details about the error. You'll want to review the event log immediately after the error.
Use the Event Viewer before and after you make a major change to the system. Inspect the event logs before installing software, hardware, or making a major configuration change. Then, after a short interval, view the event logs again to see if the change is causing warning or error events.
Review the event logs periodically to learn about problems that may not be apparent from the operation of the computer, but can become serious if not attended to.
Set Event Log Options
You can set several Event Log options to aid in troubleshooting and improve Windows performance. In the left pane of Event Viewer right-click on one of the event logs and select Properties in the popup menu. The log's Properties dialog box will appear.
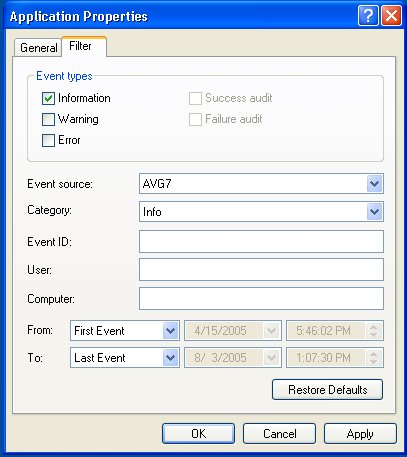 On the [Filter] tab you can configure the Event Viewer to filter out specific event types from specific Sources. Then you won't need to scroll through a long list of events to view the events caused by the source you are investigating. For example, you might to filter out all Information and Warning event types from all sources in order to focus on only the Error type events.
On the [Filter] tab you can configure the Event Viewer to filter out specific event types from specific Sources. Then you won't need to scroll through a long list of events to view the events caused by the source you are investigating. For example, you might to filter out all Information and Warning event types from all sources in order to focus on only the Error type events.
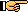 After you fix the problem causing Error events, use the filter to select and delete all related events so when you check the log later you won't be confused. You can also select to clear all events.
After you fix the problem causing Error events, use the filter to select and delete all related events so when you check the log later you won't be confused. You can also select to clear all events.
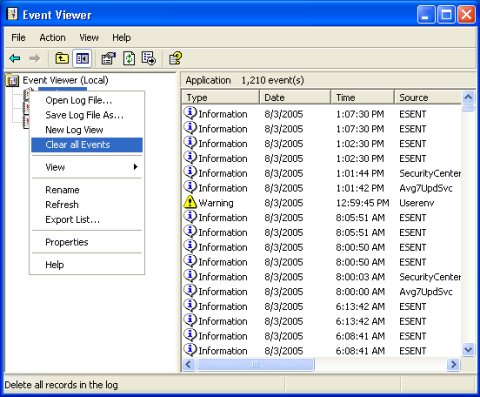 The default size of a log is 512 KB. There is no reason to maintain such large logs. In the log's Properties dialog box, on the [General] tab, in the Log size section, set the Maximum log size to 64 KB.
The default size of a log is 512 KB. There is no reason to maintain such large logs. In the log's Properties dialog box, on the [General] tab, in the Log size section, set the Maximum log size to 64 KB.
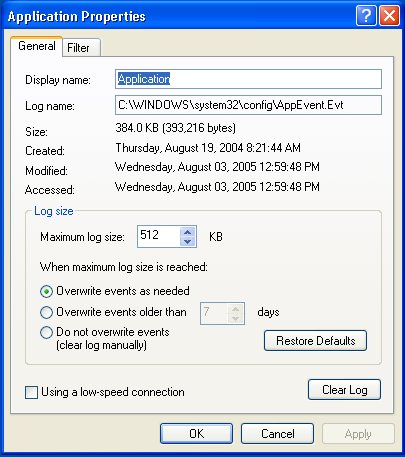
In order to maintain the log size at 64 KB, when a new event occurs, the oldest event will be overwritten. An alternative configuration would be to leave the log size at 512 KB, but set the log to overwrite events older than a certain date. You can also configure it to allow you to clear events manually.
Security Log
Each time you logon or logoff the system, a Security event is created. In a corporate network environment, system administrators will regularly analyze the Security log for signs of hacker activity. There are third party applications that can perform this analysis for them.
 You might find it interesting to know that it's not just user logon that create Security events. Software applications and even Windows services need permission to access a systems resources.
You might find it interesting to know that it's not just user logon that create Security events. Software applications and even Windows services need permission to access a systems resources.
Anything noteworthy that happens in Windows is recorded in an "event log". Most people ignore these logs; however, they can be very useful for troubleshooting purposes.
- Some applications create their own separate event log which is displayed in Event Viewer along with Windows standard Application, Security and System event logs. Sometimes an aplication will leave its event log behind after you uninstall it. You can remove the log by removing its subkey from the key:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Eventlog
Also remove the associated file from the folder:\Windows\system32\config
It will have an .evt extension. But never remove AppEvent.evt, SecEvent.evt, or SysEvent.evt, the Application, Security and System event logs.
To view an event log, in Control Panel select the Administrative Tools. In the Administrative Tools window, select the Event Viewer. You can also open Event Viewer by selecting Start | Run and typing eventvwr.msc in the Run dialog box.

An Error event records that a critical error has occurred. You might want to investigate an Error event before it becomes a more serious problem. To view the details of an event, double-click on the event in the list. The Event Properties dialog box will open. The Event Properties dialog box Description section will display a description of the event, and maybe a link to a source of more information about that type of event.

How to Use Event Description Information
The information provided by the Event Properties dialog box should point you towards the source of the problem. Use your regular troubleshooting tools, resources, and techniques to solve the problem.
If the Event Properties dialog box includes a link to Micosoft's website (and your computer is connected to the Internet), click on the link. This will execute the Microsoft Help and Support Center which will retrieve information related to the error from Microsoft's web site. This information may include instructions about how to solve the problem, along with links to relevant information on Microsoft's web site.
You can also visit the Microsoft Knowledge Base where you can search for information by typing the error description or a question into the search box. You can also type the error description into a general search engine to perform a general web search.
When to Use Event Viewer
Use the Event Viewer when an error occurs while using your computer. Windows will generate an Error event log proving details about the error. You'll want to review the event log immediately after the error.
Use the Event Viewer before and after you make a major change to the system. Inspect the event logs before installing software, hardware, or making a major configuration change. Then, after a short interval, view the event logs again to see if the change is causing warning or error events.
Review the event logs periodically to learn about problems that may not be apparent from the operation of the computer, but can become serious if not attended to.
Set Event Log Options
You can set several Event Log options to aid in troubleshooting and improve Windows performance. In the left pane of Event Viewer right-click on one of the event logs and select Properties in the popup menu. The log's Properties dialog box will appear.



In order to maintain the log size at 64 KB, when a new event occurs, the oldest event will be overwritten. An alternative configuration would be to leave the log size at 512 KB, but set the log to overwrite events older than a certain date. You can also configure it to allow you to clear events manually.
Security Log
Each time you logon or logoff the system, a Security event is created. In a corporate network environment, system administrators will regularly analyze the Security log for signs of hacker activity. There are third party applications that can perform this analysis for them.
Anything noteworthy that happens in Windows is recorded in an "event log". Most people ignore these logs; however, they can be very useful for troubleshooting purposes.
Build your own computer
Introduction
In this tutorial I will try an teach you how to successfully build your own computer! There are many benefits to building your own computer.
- You get hand's on experience learning how a computer works
- Its a hell of alot less expensive then buying one from a retailer
- Its a hell of alot more reliable than buying one from a retailer being that you hand select QUALITY parts and put it togethor yourself.
- You can do your own tech support no more relying on stupid Best Buy Tech's that don't know the difference between their ass and a hard disk jumper (don't worry I'll tell you what those are later)
Here we will discuss a list of the parts you need and the best place to purchase them. If you want the best
prices on computer hardware you will definitly want to look online. Unfortunatly (and for some of you very fortunatly
if you know what I mean) this requires the use of a credit card. Below is a general list of the devices you will
need...
- A Computer Case (Something To Put All The Computer Parts Togethor In)
- Should only run you about 50 dollars
- Beware the cheap ones with cheap power supplies they will die in a year
- A Mother Board (Everything Will Be Plugged Into The Mother Board)
- A Floppy Drive and a CDROM (Should Be Obvious)
- A Hard Disk (Come In Many Different Flavors and Quality Levels, Stores All The Information In Your Computer)
- A Video Card (Cheap Stuff, Its What Your Monitor Plugs Into)
- IDE Controller Ribbon
- Miscellaneous Accessories
may vary depending on which Operating Systems you plan on running.
Section #2 (Which Brand And Model Should I Buy?)
We'll lets start with your computer case and move all the way down to Miscellaneous Accessories..
1. Computer Case
You will most certainly need an ATX style case with a quality power supply. How do you tell? Well if the case
is only 15-20 bucks theres a pretty good chance its a crappy power supply.
2. A Mother Board
I suggest a quality ASUS (ATX style to match your computer case) mother board its up to you ask your friends.
I've had bad experiences personally with FIC
mother boards.
3. A Floppy Drive and CDROM
Pretty inexpensive stuff, i'd suggest a Sony Floppy drive and a generic CDROM. Doesn't make too much a difference if your
concerned about getting the best price.
4. Hard Disks
Gets alittle tricky. If you want reliability, high speed transfers, and are willing to run Windows I suggest a Western Digital
or a Seagate ULTRA DMA-66. If your not to concerned with speed and want to run a server with Unix i'd go with a Fujitsu or
a Western Digital. Their farely inexpensive but only transfer in 33 megabit bursts as apposed to the DMA-66 which transfer
in 33 megabit bursts. I don't believe Unix currently supports ULTRA DMA-66, but don't quote me on that. Now there's an even faster
transfer rate available via SCSI Hard Disk Controllers, but i'm not about to go into setting up SCSI controllers in this tutorial.
For now we will stick with IDE Hard Disk controllers.
5. Video Cards
Video cards are cheap and if your not a gamer a plain ole gener Cirrus Logic or STB video card will do fine.
6. IDE Controller Ribbon
You'll need 2 different kinds of IDE Ribbon 2 40 pins for your CDROM and Hard Disk and Another with less pins for your floppy.
You can buy these at any local computer store or order them off the web.
7. Miscellaneous Stuff
You may be interested in adding a sound card, ethernet card, and/or 3DFX card to your system. These are relatively easy to do and
I will explain how to add card's to your mother board later.
Section #3 (Where do I buy all this crap!?)
Well if your looking for the best prices online for computer hardware (and this is my unbiast opinion) i'd suggest going to
http://www.pricewatch.com again ask your friends maybe they know a better place. Pricewatch.com researchs the best prices
on computer hardware.
Section #4 (Lets Assemble!)
This next part is very important so read carefully...
- First things first get yourself a clean desk to work on.
- Place your ATX stlye computer case on the desk and slide/lift the top off. Inside should be a bunch of wires coming out
of the power supply in the back and a bunch of wires coming out near the face of the box.
- The next thing your going to want to do is place your mother board inside the case and fasten it in. Their might be
metal coverings covering the holes in the computer case were the parralel ports and serial ports on the mother board
should poke through, go ahead and poke those out with a screw drive so you can fit the mother board in snuggly. Every
Case fastens mother boards in different ways. Some use plastic pegs, some use metal screws. It will hopefully be obvious
which you have to use.
- #4 Once the mother board is mounted properly you will need to fasten the floppy drive, and cdrom into the computer case.
All computer cases store floppy drives differently there maybe a slide out container that you screw them into. You'll
have to make sure that the the floppy drive is right side up (duh!) and that the pins are facing towards the back of the
computer. Installing the CDROM is pretty much the same in all computer cases. Some mounting rails should have come
with your mother board. You need to fasten those to the sides of the CDROM and you should be able to slide it right in
to one of the top bays.
- Insert your Video Card. There are presently about 3 differnet forms of slots on your mother board. PCI, ISA, and AGP.
Video Cards are presently made for all 3 of them. AGP stands for "Accelrated Graphics Port" Video Cards made for this
slot are generally more high tech/performance. PCI's work and so do ISA (Althoug ISA is more Old School). Gee how
do I tell the difference? Well AGP slots more than likely is the only small, brown, slot on your mother board. PCI
you probably have the most of these their white and little longer than AGP. ISA, these are longggg and black, ugly.
Insert your Video Card and snug it in there firmly. Don't force it (duh).
- Time for that evil Hard Disk installation. We'll Hit hooking up the power supplies and Installing the Hard Disk at the
same time just for fun. Insert the Hard Disk In a very much similar way to the way you inserted the floppy disk. But
Before you do make sure that the jumper settings are correct on the back of Har Disk. Most hard disks are shipped in
single mode, but if you want to run multiple hard disks (which we won't discuss) you need to set the jumpers differently.
Jumpers are little metal prongs connected with little jumpers that complete a connection. You figure it out. Anyway
you got your hard disk in now its time to hook up the power supplies. The hard disk and the CDROM have similar power supp
lies. 3 or 4 prong. Hook those funny looking cords coming out of the back of the power supply into your CDROM and Hard
Disk. Theres a smaller one that hooks into your floppy it should be obvious. Theres a big power supply (the biggest one
in the lot usually made of white plastic) It fits into a slot on your mother board, it is the main power supply to your
mother board. Its kind of tricky to get in so be careful.
- Now that you have your Power Supplies hooked up you'll need to connect your Periphrials to your Mother Board. Use the IDE
Controller Ribbon I know you all have. Hey one end goes to your CDROM (make sure the red line on the ribbon "pin 1" is
matched up with the first pin on the back of your CDROM) and the other end goes to your mother board (same deal). The
same goes for your hard disk and yoru floppy. Figure it out its not that difficult. You'll know you did something wrong
when you get a floppy disk fail on boot.
- Finishing touches. Don't forget to connect those nasty wires coming out from behind the face of your computer case to
your mother board. They control the on, off, reset, hard disk activity, and power switch. Every mother board is different
so i hope you have a manual with your mother board. Most specify with 2 or 3 character paraphrases that make no sense.
For Example "PWR SWT" = Power Switch "RST SWT" = Reset Switch. Or even more vague than that.
Ok your ready to give it a whirl, you'll need to get in your system bios. The "DEL" key should usually get you in.
Get it to autodetect your hard disk. Accept the Setting and Save your Configurations. Install Your OS and your ready to go.
That easy!! Ha! you'll prolly have lots of trouble theres a million resources online to help you. Get to it.
BASIC C Socket Programming In Unix For Newbies
CONTENTS
=======================================
1. Introduction
2. Different types of Internet Sockets
3. Structures
4. Conversions
5. IP Addresses
6. Important Functions
6.1. socket()
6.2. bind()
6.3. connect()
6.4. listen()
6.5. accept()
6.6. send()
6.7. recv()
6.8. sendto()
6.9. recvfrom()
6.10. close()
6.11. shutdown()
6.12. gethostname()
7. Some words about DNS
8. A Stream Server Example
9. A Stream Client Example
10. Last Words
11. Copyright
1. INTRODUCTION
=======================================
Are you trying to learn c socket programming? Or do you think that it's hard stuff?
Well, then you must read this basic tutorial to get basic ideas and concepts and to start
to work with sockets. Don't expect to be a "socket programming master" after reading this
tutorial. You'll only be that if you practice and read a lot.
2. DIFFERENT TYPES OF INTERNET SOCKETS
=======================================
In the first place I must explain what a socket is. In a very simple way, a socket is a way
to talk to other computer. To be more precise, it's a way to talk to other computers using
standard Unix file descriptors. In Unix, every I/O actions are done by writing or reading
to a file descriptor. A file descriptor is just an integer associated with an open file and it
can be a network connection, a terminal, or something else.
About the different types of internet sockets, there are many types but I'll just describe two
of them - Stream Sockets (SOCK_STREAM) and Datagram Sockets (SOCK_DGRAM).
"And what are the differences between this two types?" you may ask. Here's the answer:
Stream Sockets - they're error free; if you send through the stream socket three
items "A,B,C", they will arrive in the same order - "A,B,C" ;
they use TCP ("Transmission Control Protocol") - this protocol
assures the items' order.
Datagram Sockets - they use UDP ("User Datagram Protocol"); they're connectionless
because you don't need to have an open connection as in Stream
Sockets - you build a packet with the destination information and
send it out.
A lot more could be explained here about this two kind of sockets, but I think this is enough
to get the basic concept of socket. Understanding what a socket is and this two types of
internet sockets is a good start, but you need to learn how to "work" with them. You'll learn
it in the next sections.
3. STRUCTURES
=======================================
The purpose of this section is not to teach you structures but to tell you how are they
used in C socket programming. If you don't know what a structure is, my advice is to read
a C Tutorial and learn it. For the moment, let's just say that a structure is a data type
that is an aggregate, that is, it contains other data types, which are grouped together into
a single user-defined type.
Structures are used in socket programming to hold information about the address.
The first structure is struct sockaddr that holds socket information.
struct sockaddr{
unsigned short sa_family; /* address family */
char sa_data[14]; /* 14 bytes of protocol address */
};
But, there's another structure (struct sockaddr_in) that help you to reference to the socket's
elements.
struct sockaddr_in {
short int sin_family; /* Address family */
unsigned short int sin_port; /* Port */
struct in_addr sin_addr; /* Internet Address */
unsigned char sin_zero[8]; /* Same size as struct sockaddr */
};
Note: sin_zero is set to all zeros with memset() or bzero() (See examples bellow).
The next structure is not very used but it is defined as an union.
As you can see in both examples bellow (Stream Client and Server Client) , when I declare for
example "client" to be of type sockaddr_in then I do client.sin_addr = (...)
Here's the structure anyway:
struct in_addr {
unsigned long s_addr;
};
Finally, I think it's better talk about struct hostent. In the Stream Client Example, you can
see that I use this structure. This structure is used to get remote host information.
Here it is:
struct hostent
{
char *h_name; /* Official name of host. */
char **h_aliases; /* Alias list. */
int h_addrtype; /* Host address type. */
int h_length; /* Length of address. */
char **h_addr_list; /* List of addresses from name server. */
#define h_addr h_addr_list[0] /* Address, for backward compatibility. */
};
This structure is defined in header file netdb.h.
In the beginning, this structures will confuse you a lot, but after you start to write some
lines, and after seeing the examples, it will be easier for you understanding them. To see
how you can use them check the examples (section 8 and 9).
4. CONVERSIONS
=======================================
There are two types of byte ordering: most significant byte and least significant byte.
This former is called "Network Byte Order" and some machines store their numbers internally
in Network Byte Order.
There are two types you can convert: short and long.
Imagine you want to convert a long from Host Byte Order to Network Byte Order. What would you
do? There's a function called htonl() that would convert it =) The following functions are
used to convert :
htons() -> "Host to Network Short"
htonl() -> "Host to Network Long"
ntohs() -> "Network to Host Short"
ntohl() -> "Network to Host Long"
You must be thinking why do you need this. Well, when you finish reading this document, it will
all seems easier =) All you need is to read and a lot of practice =)
An important thing, is that sin_addr and sin_port (from struct sockaddr_in) must be in Network
Byte Order (you'll see in the examples the functions described here to convert and you'll start
to understand it).
5. IP ADRESSES
=======================================
In C, there are some functions that will help you manipulating IP addresses. We'll talk about
inet_addr() and inet_ntoa() functions.
inet_addr() converts an IP address into an unsigned long. An example:
(...)
dest.sin_addr.s_addr = inet_addr("195.65.36.12");
(...)
/*Remember that this is if you've a struct dest of type sockaddr_in*/
inet_ntoa() converts string IP addresses to long. An example:
(...)
char *IP;
ip=inet_ntoa(dest.sin_addr);
printf("Address is: %s\n",ip);
(...)
Remember that inet_addr() returns the address in Network Byte Order - so you don't need to
call htonl().
6. IMPORTANT FUNCTIONS
=======================================
In this section I'll put the function' syntax, the header files you must include to call it,
and little comments. Besides the functions mentioned in this document, there are more, but
I decided to put only these ones here. Maybe I'll put them in a future version of this
document =) To see examples of these functions, you can check the stream client and stream
server source code (Sections 8 and 9)
6.1. socket()
=============
#include
#include
int socket(int domain,int type,int protocol);
Let's see the arguments:
domain -> you can set "AF_INET" (set AF_INET to use ARPA internet protocols)
or "AF_UNIX" if you want to create sockets for inside comunication.
Those two are the most used, but don't think that there are just
those. There are more I just don't mention them.
type -> here you put the kind of socket you want (Stream or Datagram)
If you want Stream Socket the type must be SOCK_STREAM
If you want Datagram Socket the type must be SOCK_DGRAM
protocol -> you can just set protocol to 0
socket() gives you a socket descriptor that you can use in later system calls or
it gives you -1 on error (this is usefull for error checking routines).
6.2. bind()
===========
#include
#include
int bind(int fd, struct sockaddr *my_addr,int addrlen);
Let's see the arguments:
fd -> is the socket file descriptor returned by socket() call
my_addr -> is a pointer to struct sockaddr
addrlen -> set it to sizeof(struct sockaddr)
bind() is used when you care about your local port (usually when you use listen() )
and its function is to associate a socket with a port (on your machine). It returns
-1 on error.
You can put your IP address and your port automatically:
server.sin_port = 0; /* bind() will choose a random port*/
server.sin_addr.s_addr = INADDR_ANY; /* puts server's IP automatically */
An important aspect about ports and bind() is that all ports bellow 1024 are reserved.
You can set a port above 1024 and bellow 65535 (unless the ones being used by other
programs).
6.3. connect()
==============
#include
#include
int connect(int fd, struct sockaddr *serv_addr, int addrlen);
Let's see the arguments:
fd -> is the socket file descriptor returned by socket() call
serv_addr -> is a pointer to struct sockaddr that contains destination IP
address and port
addrlen -> set it to sizeof(struct sockaddr)
connect() is used to connect to an IP address on a defined port. It returns -1 on
error.
6.4. listen()
=============
#include
#include
int listen(int fd,int backlog);
Let's see the arguments:
fd -> is the socket file descriptor returned by socket() call
backlog -> is the number of allowed connections
listen() is used if you're waiting for incoming connections, this is, if you want
someone to connect to your machine. Before calling listen(), you must call bind()
or you'll be listening on a random port =) After calling listen() you must call
accept() in order to accept incoming connection. Resuming, the sequence of system calls
is:
1. socket()
2. bind()
3. listen()
4. accept() /* In the next section I'll explain how to use accept() */
As all functions above described, listen() returns -1 on error.
6.5. accept()
=============
#include
int accept(int fd, void *addr, int *addrlen);
Let's see the arguments:
fd -> is the socket file descriptor returned by listen() call
addr -> is a pointer to struct sockaddr_in where you can determine which host
is calling you from which port
addrlen -> set it to sizeof(struct sockaddr_in) before its address is passed
to accept()
When someone is trying to connect to your computer, you must use accept() to get the
connection. It's very simple to understand: you just get a connection if you accept =)
Next, I'll give you a little example of accept() use because it's a little different
from other functions.
(...)
sin_size=sizeof(struct sockaddr_in);
if ((fd2 = accept(fd,(struct sockaddr *)&client,&sin_size))==-1){ /* calls accept() */
printf("accept() error\n");
exit(-1);
}
(...)
From now on, fd2 will be used for add send() and recv() calls.
6.6. send()
===========
int send(int fd,const void *msg,int len,int flags);
Let's see the arguments:
fd -> is the socket descriptor where you want to send data to
msg -> is a pointer to the data you want to send
len -> is the length of the data you want to send (in bytes)
flags -> set it to 0
This function is used to send data over stream sockets or CONNECTED datagram sockets.
If you want to send data over UNCONNECTED datagram sockets you must use sendto().
send() returns the number of bytes sent out and it will return -1 on error.
6.7. recv()
===========
int recv(int fd, void *buf, int len, unsigned int flags);
Let's see the arguments:
fd -> is the socket descriptor to read from
buf -> is the buffer to read the information into
len -> is the maximum length of the buffer
flags -> set it to 0
As I said above about send(), this function is used to send data over stream sockets or
CONNECTED datagram sockets. If you want to send data over UNCONNECTED datagram sockets
you must use recvfrom().
recv() returns the number of bytes read into the buffer and it'll return -1 on error.
6.8. sendto()
=============
int sendto(int fd,const void *msg, int len, unsigned int flags,
const struct sockaddr *to, int tolen);
Let's see the arguments:
fd -> the same as send()
msg -> the same as send()
len -> the same as send()
flags -> the same as send()
to -> is a pointer to struct sockaddr
tolen -> set it to sizeof(struct sockaddr)
As you can see, sendto() is just like send(). It has only two more arguments : "to"
and "tolen" =)
sendto() is used for UNCONNECTED datagram sockets and it returns the number of bytes
sent out and it will return -1 on error.
6.9. recvfrom()
===============
int recvfrom(int fd,void *buf, int len, unsigned int flags
struct sockaddr *from, int *fromlen);
Let's see the arguments:
fd -> the same as recv()
buf -> the same as recv()
len -> the same as recv()
flags -> the same as recv()
from -> is a pointer to struct sockaddr
fromlen -> is a pointer to a local int that should be initialised
to sizeof(struct sockaddr)
recvfrom() returns the number of bytes received and it'll return -1 on error.
6.10. close()
=============
close(fd);
close() is used to close the connection on your socket descriptor. If you call close(),
it won't be no more writes or reads and if someone tries to read/write will receive an
error.
6.11. shutdown()
================
int shutdown(int fd, int how);
Let's see the arguments:
fd -> is the socket file descriptor you want to shutdown
how -> you put one of those numbers:
0 -> receives disallowed
1 -> sends disallowed
2 -> sends and receives disallowed
When how is set to 2, it's the same thing as close().
shutdown() returns 0 on success and -1 on error.
6.12. gethostname()
===================
#include
int gethostname(char *hostname, size_t size);
Let's see the arguments:
hostname -> is a pointer to an array that contains hostname
size -> length of the hostname array (in bytes)
gethostname() is used to get the name of the local machine.
7. SOME WORDS ABOUT DNS
=======================================
I created this section, because I think you should know what DNS is. DNS stands for "Domain
Name Service" and basically, it's used to get IP addresses. For example, I need to know the
IP address of queima.ptlink.net and through DNS I'll get 212.13.37.13 .
This is important, because functions we saw above (like bind() and connect()) work with IP
addresses.
To see you how you can get queima.ptlink.net IP address on c, I made a little example:
/* <---- SOURCE CODE STARTS HERE ----> */
#include
#include
#include
#include
#include
int main(int argc, char *argv[])
{
struct hostent *he;
if (argc!=2){
printf("Usage: %s
exit(-1);
}
if ((he=gethostbyname(argv[1]))==NULL){
printf("gethostbyname() error\n");
exit(-1);
}
printf("Hostname : %s\n",he->h_name); /* prints the hostname */
printf("IP Address: %s\n",inet_ntoa(*((struct in_addr *)he->h_addr))); /* prints IP address */
}
/* <---- SOURCE CODE ENDS HERE ----> */
8. A STREAM SERVER EXAMPLE
=======================================
In this section, I'll show you a nice example of a stream server. The source code is all
commented so that you ain't no possible doubts =)
Let's start:
/* <---- SOURCE CODE STARTS HERE ----> */
#include
#include
#include
#include
#define PORT 3550 /* Port that will be opened */
#define BACKLOG 2 /* Number of allowed connections */
main()
{
int fd, fd2; /* file descriptors */
struct sockaddr_in server; /* server's address information */
struct sockaddr_in client; /* client's address information */
int sin_size;
if ((fd=socket(AF_INET, SOCK_STREAM, 0)) == -1 ){ /* calls socket() */
printf("socket() error\n");
exit(-1);
}
server.sin_family = AF_INET;
server.sin_port = htons(PORT); /* Remember htons() from "Conversions" section? =) */
server.sin_addr.s_addr = INADDR_ANY; /* INADDR_ANY puts your IP address automatically */
bzero(&(server.sin_zero),8); /* zero the rest of the structure */
if(bind(fd,(struct sockaddr*)&server,sizeof(struct sockaddr))==-1){ /* calls bind() */
printf("bind() error\n");
exit(-1);
}
if(listen(fd,BACKLOG) == -1){ /* calls listen() */
printf("listen() error\n");
exit(-1);
}
while(1){
sin_size=sizeof(struct sockaddr_in);
if ((fd2 = accept(fd,(struct sockaddr *)&client,&sin_size))==-1){ /* calls accept() */
printf("accept() error\n");
exit(-1);
}
printf("You got a connection from %s\n",inet_ntoa(client.sin_addr) ); /* prints client's IP */
send(fd2,"Welcome to my server.\n",22,0); /* send to the client welcome message */
close(fd2); /* close fd2 */
}
}
/* <---- SOURCE CODE ENDS HERE ----> */
9. A STREAM CLIENT EXAMPLE
=======================================
/* <---- SOURCE CODE STARTS HERE ----> */
#include
#include
#include
#include
#include
#define PORT 3550 /* Open Port on Remote Host */
#define MAXDATASIZE 100 /* Max number of bytes of data */
int main(int argc, char *argv[])
{
int fd, numbytes; /* files descriptors */
char buf[MAXDATASIZE]; /* buf will store received text */
struct hostent *he; /* structure that will get information about remote host */
struct sockaddr_in server; /* server's address information */
if (argc !=2) { /* this is used because our program will need one argument (IP) */
printf("Usage: %s
exit(-1);
}
if ((he=gethostbyname(argv[1]))==NULL){ /* calls gethostbyname() */
printf("gethostbyname() error\n");
exit(-1);
}
if ((fd=socket(AF_INET, SOCK_STREAM, 0))==-1){ /* calls socket() */
printf("socket() error\n");
exit(-1);
}
server.sin_family = AF_INET;
server.sin_port = htons(PORT); /* htons() is needed again */
server.sin_addr = *((struct in_addr *)he->h_addr); /*he->h_addr passes "*he"'s info to "h_addr" */
bzero(&(server.sin_zero),8);
if(connect(fd, (struct sockaddr *)&server,sizeof(struct sockaddr))==-1){ /* calls connect() */
printf("connect() error\n");
exit(-1);
}
if ((numbytes=recv(fd,buf,MAXDATASIZE,0)) == -1){ /* calls recv() */
printf("recv() error\n");
exit(-1);
}
buf[numbytes]='\0';
printf("Server Message: %s\n",buf); /* it prints server's welcome message =) */
close(fd); /* close fd =) */
}
/* <---- SOURCE CODE ENDS HERE ----> */
10. LAST WORDS
=======================================
As I'm just a simple human, it's almost certain that there are some errors on this document.
When I say errors I mean English errors (because my language is not the English) but also
technical errors. Please email me if you detect any error =)
But you must understand that this is the first version of this document, so , it's natural not
to be very complete (as matter of fact I think it is ) and it's also very natural to have
stupid errors. However, I can be sure that source code presented in this document works fine.
If you need help concerning this subject you can email me at
SPECIAL THANKS TO: Ghost_Rider (my good old mate), Raven (for letting me write this tutorial)
and all my friends =)
Subscribe to:
Posts (Atom)





















