Tuesday, August 17, 2010
Public DNS Service from Google
Google is on its way to establish monopoly on the Internet with the public DNS service.DNS (Domain Name System) in simple word is a set of protocols that translates IP address into names.Every computer on the Internet has an IP address.Thus, the server which is to be accessed by the client, must have have its IP address translated to a name.Like, when we type www.google.com it points to the IP address of the Google server.
Google Public DNS is a free, global Domain Name System (DNS) resolution service, that one can use as an alternative to current DNS provider.
http://code.google.com/speed/public-dns/
Top Five Tips to Secure Website
A secure website is always essential ingredient of peace of mind for both web-master and the end user.These days hundreds of website come alive on the Internet because of high competition and >web hosting that comes with cheap price tag.But, what people do not understand is value of hack-proof website.Recently, according to a survey conducted by PricewaterhouseCoopers in the year 2009, companies are reducing their security related costs primarily due to recession.But, the number no. of victims is growing without any hurdle.This clearly indicates immense need for security.This post describes few most basic yet powerful ways to curb any hazard to your websites.
1)Vulnerability Assessment
A vulnerability scanner is a tool that searches and maps a system or network for different possible weakness and report it with feedback for the use of administrator.They can give you possible web application vulnerabilities like sql injection, XSS and firewall security breach.Nikto is a very useful open source scanner and also you can use Acunetix Web Vulnerability scanner.
2)Penetration Testing
This is part of security testing in which a deliberate and simulated attack is carried out to circumvent security of a system.This is a must to be deployed step for commercial websites.Security can not be full-proof, as secured wordpress web hosting can be compromised with c99 madshell script written in php.
3)Web Application Firewalls
Web application firewalls are essential for larger and advanced websites as these can not be affordable by everyone.These firewalls are specifically designed for fine tuning web application by keeping a check on HTTP traffic and data leakage by residing in between client and server.
4)Client Security Tools
A web-master can do everything from his part to secure a server.But, risk management has to be one of the most important priority.One can never predict about security in the future.So, clients have to advised by web-masters to use some of browser security tool to save themselves from any loss.Such a tool can be XSS me FireFox add on or Internet Explorer 8's in built XSS filter.
5)Application Whitelists
It is a policy that is employed by administrators to document congiguration pf applications put in the whitelist.This way they can detect any unauthorized changes to the server environment.
These are the five ways to put a secured website on the Internet.But, all these are not affordable by everyone.You must be aware of Internet mobs.While choosing a CMS for your website go for something that gets updated quickly with larger user base like Joomla, Nuke, drupal web hosting etc.
1)Vulnerability Assessment
A vulnerability scanner is a tool that searches and maps a system or network for different possible weakness and report it with feedback for the use of administrator.They can give you possible web application vulnerabilities like sql injection, XSS and firewall security breach.Nikto is a very useful open source scanner and also you can use Acunetix Web Vulnerability scanner.
2)Penetration Testing
This is part of security testing in which a deliberate and simulated attack is carried out to circumvent security of a system.This is a must to be deployed step for commercial websites.Security can not be full-proof, as secured wordpress web hosting can be compromised with c99 madshell script written in php.
3)Web Application Firewalls
Web application firewalls are essential for larger and advanced websites as these can not be affordable by everyone.These firewalls are specifically designed for fine tuning web application by keeping a check on HTTP traffic and data leakage by residing in between client and server.
4)Client Security Tools
A web-master can do everything from his part to secure a server.But, risk management has to be one of the most important priority.One can never predict about security in the future.So, clients have to advised by web-masters to use some of browser security tool to save themselves from any loss.Such a tool can be XSS me FireFox add on or Internet Explorer 8's in built XSS filter.
5)Application Whitelists
It is a policy that is employed by administrators to document congiguration pf applications put in the whitelist.This way they can detect any unauthorized changes to the server environment.
These are the five ways to put a secured website on the Internet.But, all these are not affordable by everyone.You must be aware of Internet mobs.While choosing a CMS for your website go for something that gets updated quickly with larger user base like Joomla, Nuke, drupal web hosting etc.
Monday, August 16, 2010
What is a drive-by download?
A drive-by download is a program that is automatically downloaded to your computer without your consent or even your knowledge. Unlike a pop-up download, which asks for assent (albeit in a calculated manner likely to lead to a "yes"), a drive-by download can be initiated by simply visiting a Web site or viewing an HTML e-mail message. If your computer's security settings are lax, it may be possible for drive-by downloads to occur without any further action on your part.
Frequently, a drive-by download is installed along with a user-requested application. (In this case, the unwanted application is sometimes called a barnacle.) For example, a file sharing program might include a spyware program that tracks and reports user information for targeted marketing purposes. An associated adware program can then generate pop-up advertisements using that information.
Xupiter, an Internet Explorer toolbar program, was frequently installed as a drive-by download in the early 2000s. The program replaced a user's home page, changed browser settings, and used a redirect to take all searches to the Xupiter Web site. In some versions, the program initiated drive-by downloads of other programs. Furthermore, although it came with an uninstall utility, Xupiter was quite challenging for the average computer user to remove.
Drive-by downloads continue to be a major security issue online. In April 2007, researchers at Google discovered hundreds of thousands of Web pages that initiated drive-by downloads. One in ten pages was found to be suspect. Sophos researchers in 2008 reported that they were discovering more than 6,000 new infected Web pages every day, or about one every 14 seconds. Many of these infections are connected to botnets, in which each PC is turned into a zombie that may then be directed to further malicious activity, like spam or DDoSWhat is a drive-by download? attacks.
Lock Your Desktop in Windows XP
If your computer is easily accessible by others and you do not wish for this to happen, you can easily lock it so that it is password protected. No one else will have access to it until you give them the required information. Here is how you do so.
Instructions
Things You'll Need:
- Windows XP
- Step 1Make sure you know the password to your computer.
- Step 2Press Ctrl+Alt+Del on your keyboard.
- Step 3Choose "Lock Desktop."
- Step 4Your computer will be locked immediately.
- Step 5If you need access to your desktop again, press Ctrl+Alt+Del.
- Step 6Enter your password and you will then be able to resume activity on the computer.
Sunday, August 15, 2010
Secretly Hide Any File Inside JPG Image File
Few months ago , USA Today story claimed that al-Qaeda operatives were sending out encrypted messages by hiding them inside digital photographs [jpg files] on eBay.
While the claim was never proved, it is very easy to hide [or embed] any other file[s] inside a JPEG image. You can place video clips, pdf, mp3, Office documents, zipped files, webpage or any other file format inside a JPEG image.
And when a suspecting user [read CIA, FBI] tries to open that jpeg file [with concealed information] in either a photo editing software or as a thumbnail inside Windows Explorer, it would be tough to make out if this camouflaged jpg file is different from any standard jpg image.
Let's say you want to hide a confidential PDF document from the tax investigation officers. What you can do is convert that file into a regular jpg image so even if anyone double-clicks this file, all he will see is a preview of the image and nothing else. And when you want to work on the actual PDF, just rename the extension from jpg to pdf.
Here's the full trick:
Step 1: You will need two files - the file you want to hide and one jpg image - it can be of any size or dimensions. [If you want to hide multiple files in one jpeg image, just zip them into one file]
Step 2: Copy the above two files to the C: folder and open the command prompt window.
Step 3: Move to the c: root by typing cd \ [if the files are in another folder, you'll have to change the prompt to that folder]
Step 4: The most important step - type the following command:
copy /b myimage.jpg + filetohide.pdf my_new_image.jpg
To recover the original PDF file, just rename my_new_image.jpg to filename.pdf.
Here we illustrated with an pdf file as that works with simple renaming. If you want to apply this technique to other file formats like XLS, DOC, PPT, AVI, WMV, WAV, SWF, etc, you may have to first compress them in RAR format before executing the copy /b DOS command.
To restore the original file, rename the .jpg file to .rar and extract it using 7-zip or Winrar.
Stupid Command Prompt Tricks
Windows XP isn't known for its powerful command line interface. Still, one of the first things I do on any fresh Windows install is set up the "Open Command Window Here" right click menu. And hoary old cmd.exe does have a few tricks up its sleeve that you may not know about.

The first thing you'll want to do is Start, Run, cmd.exe, then right click the window menu and choose properties. Be sure to enable the following quality of life improvements:
And of course, set the font and colors to taste. I use green-screen style colors (background 0 55 0, foreground 0 255 0) with Lucida Console as pictured above. But if you prefer Comic Sans here, be my guest! When exiting this dialog, you'll be prompted to save. Make sure you select "Save properties for future windows with same title" so all future command prompts will benefit from these improved settings.
There are also a few helpful keyboard shortcuts that aren't always widely known:
The first thing you'll want to do is Start, Run, cmd.exe, then right click the window menu and choose properties. Be sure to enable the following quality of life improvements:
- Options | Command History | Buffer Size | 500
- Options | Command History | Discard Old Duplicates | True
- Options | Edit Options | QuickEdit Mode | True
- Layout | Screen buffer size | Height | 999
- Layout | Window size | Height | 50
And of course, set the font and colors to taste. I use green-screen style colors (background 0 55 0, foreground 0 255 0) with Lucida Console as pictured above. But if you prefer Comic Sans here, be my guest! When exiting this dialog, you'll be prompted to save. Make sure you select "Save properties for future windows with same title" so all future command prompts will benefit from these improved settings.
There are also a few helpful keyboard shortcuts that aren't always widely known:
- Pressing arrow up selects a previous command from your command history; similarly, arrow down selects the next command.
- Pressing F7 pops up your command history list.
- You can drag n' drop files or folders from an explorer window into a command prompt; this inserts the quoted path as if you had manually pasted it.
- Tab completion is fully supported; type edit *.ini then hit TAB to iterate through all matches. Use SHIFT+TAB to move to the previous match. This works for partial filenames as you would expect, and in all commands.
- Tired of the typical "c:\windows\system32\cmd.exe" window title? Change it using the TITLE command.
- ALT+ENTER takes your command prompt to fullscreen mode and back again.
Some Command Prompt Tricks
Last night i was cleaning Junk from my PC. Because .. I test lots of freewares to find out best freeware programs for my needs. Then i found found some Command Prompt tricks i collected few years ago. This trick are Old but still.. If you want to have some fun with command prompt , here is some…
Watch A Movie Created with Command Prompt
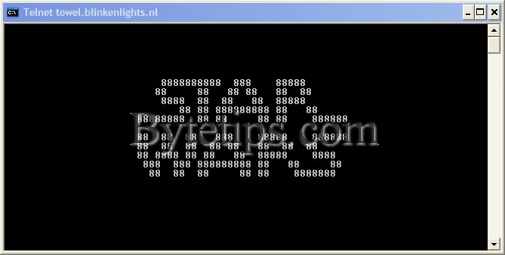 Command prompts movie..!! amazing Creation. But you need active internet connection to enjoy this movie. It’s a star wars movie. Here is how to watch this movie :
Command prompts movie..!! amazing Creation. But you need active internet connection to enjoy this movie. It’s a star wars movie. Here is how to watch this movie :
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
And hit Enter. Now enjoy the Star wars Movie.
Shutdown PC On your LAN Network
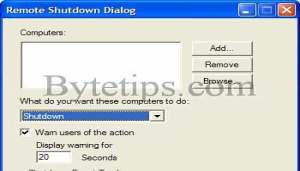 This trick will shutdown a selected pc from Your LAN network. You can apply this trick in your office or school.. but i take no responsibilities fro any action. Its just for fun. Here is how to use this trick :
This trick will shutdown a selected pc from Your LAN network. You can apply this trick in your office or school.. but i take no responsibilities fro any action. Its just for fun. Here is how to use this trick :
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
And hit Enter. You will see remote shutdown Window. If you know someone’s IP on a computer in your Local Area network, type in their IP Address after clicking the add button.
3. After entering the IP Address click OK . Now watch the person’s face as their computer shuts down.
Some users have asked me that they got Access Denied error for remote shutdown. Add the user with the privilege to force a remote shutdown on the computer you are about to Shutdown.To do this go to control panel > Administrative Tools > Local Security Settings. Now go to Security Settings > Local Policies > User Rights Assignment. Double-click on Force shutdown from a remote system in the right pane and Click on Add User or Group. Add the computer that runs the remote shutdown command.
Or you can do this go the computer you are about to Shutdown
a) Go to Start > Run > type in Regedit in the dialog box and hit enter
b) Go to My Computer/HKEY_LOCAL_MACHINE /system/currentcontrolset/control/lsa
c) Find “forceguest” in the right pane Double click on it to modify This entry change the value from “1″ entry to “0″
Some Other Fun on Command Prompt
At first start command prompt from Start > Run, the type in cmd click on OK and enter the following command:
Here your Custom Message indicates any message. Then hit Enter check out the title bar of
the command window. Just a cheap little trick…
Here is another.. Run command prompt and type in
For example if you type prompt hello your c: prompt will change to hello
That’s all for now Have fun and enjoy..
Watch A Movie Created with Command Prompt

STAR WARS MOVIE
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
telnet towel.blinkenlights.nlAnd hit Enter. Now enjoy the Star wars Movie.
Shutdown PC On your LAN Network

Remote Shutdown
1. Go to Start > Run and type in cmd
2. You will see the command prompt window . Now type in this command line.
shutdown.exe -iAnd hit Enter. You will see remote shutdown Window. If you know someone’s IP on a computer in your Local Area network, type in their IP Address after clicking the add button.
3. After entering the IP Address click OK . Now watch the person’s face as their computer shuts down.
Some users have asked me that they got Access Denied error for remote shutdown. Add the user with the privilege to force a remote shutdown on the computer you are about to Shutdown.To do this go to control panel > Administrative Tools > Local Security Settings. Now go to Security Settings > Local Policies > User Rights Assignment. Double-click on Force shutdown from a remote system in the right pane and Click on Add User or Group. Add the computer that runs the remote shutdown command.
Or you can do this go the computer you are about to Shutdown
a) Go to Start > Run > type in Regedit in the dialog box and hit enter
b) Go to My Computer/HKEY_LOCAL_MACHINE /system/currentcontrolset/control/lsa
c) Find “forceguest” in the right pane Double click on it to modify This entry change the value from “1″ entry to “0″
Some Other Fun on Command Prompt
At first start command prompt from Start > Run, the type in cmd click on OK and enter the following command:
title your Custom MessageHere your Custom Message indicates any message. Then hit Enter check out the title bar of
the command window. Just a cheap little trick…
Here is another.. Run command prompt and type in
prompt whatever you want it sayFor example if you type prompt hello your c: prompt will change to hello
That’s all for now Have fun and enjoy..
Tags for the article:
- command prompt tricks,command prompt hacks,cool command prompt tricks,cmd commands tricks,cmd prompt tricks,cmd tricks,command prompt tricks and hacks,cool cmd commands,Command promt tricks,command prompt trick
Subscribe to:
Posts (Atom)





